Microsoft Intune and Endpoint Manager: Device and Security Management
As the modern workplace shifts to a mobile and remote work model, it is critical for IT professionals to ensure the security of devices and data. Microsoft Intune and Microsoft Endpoint Manager enable organizations to centrally manage employee devices, enforce security policies, and protect data.
What is Microsoft Intune?
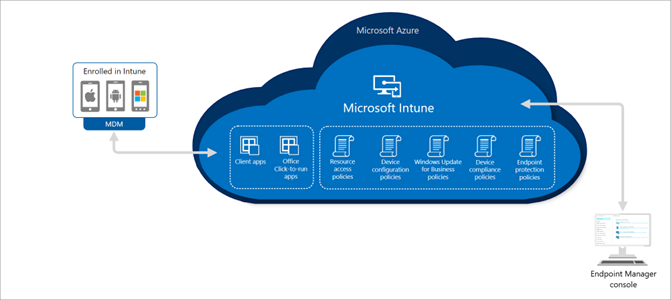
Microsoft Intune offers a cloud-based mobile device management and mobile application management solution. This service helps you centrally manage and protect Windows, macOS, iOS, Android, and Linux devices.
Key Features of Intune
Device enrollment and management – Enables you to enroll and securely manage company-owned and personal devices.
Policy enforcement – Enforces encryption, Wi-Fi, VPN, antivirus, and other security requirements on devices.
App management – Prevents data leakage by separating personal and work apps.
Conditional access – Defines user access rights and allows access only from eligible devices.
Data Protection – Remotely wipe or lock devices when they are stolen or lost.
What is Microsoft Endpoint Manager (MEM)?
Microsoft Endpoint Manager is a single platform that integrates management tools such as Intune, Configuration Manager (SCCM), Windows Autopilot, and Defender for Endpoint.
Endpoint Manager Core Services:
Microsoft Intune – Cloud-based device and application management.
Configuration Manager (SCCM) – Management of on-premises devices on the network.
Windows Autopilot – Automatically gets new devices ready for work.
Defender for Endpoint – Cybersecurity and threat detection service.
Endpoint Analytics – Analyzes device performance and improves employee experience.
How Do Microsoft Intune and Endpoint Manager Work?
Device Enrollment – Employees enroll their personal or corporate devices in Intune according to organizational policies.
App and Policy Enforcement – IT admins push apps and security rules to devices.
Monitoring and security control – Endpoint Manager tracks the real-time status of devices, applies updates, and protects against threats.
Compliance and access control – Non-compliant devices are denied or restricted access to the corporate network.
Why Microsoft Intune and Endpoint Manager?
Reduces IT workload – Devices are automatically enrolled and managed from the cloud.
Protects corporate data – Keeps corporate data safe by isolating it, even on personal devices.
Implements remote management and security measures – Remotely wipe lost or stolen devices at any time.
Ideal for hybrid and remote teams – Teams working on different devices and platforms can work without worrying about data security.
Conclusion
Microsoft Intune and Endpoint Manager provide a modern approach to securely managing corporate devices and data. With centralized management, automatic policy enforcement, and real-time security controls, organizations can keep their work environment more secure and efficient.
